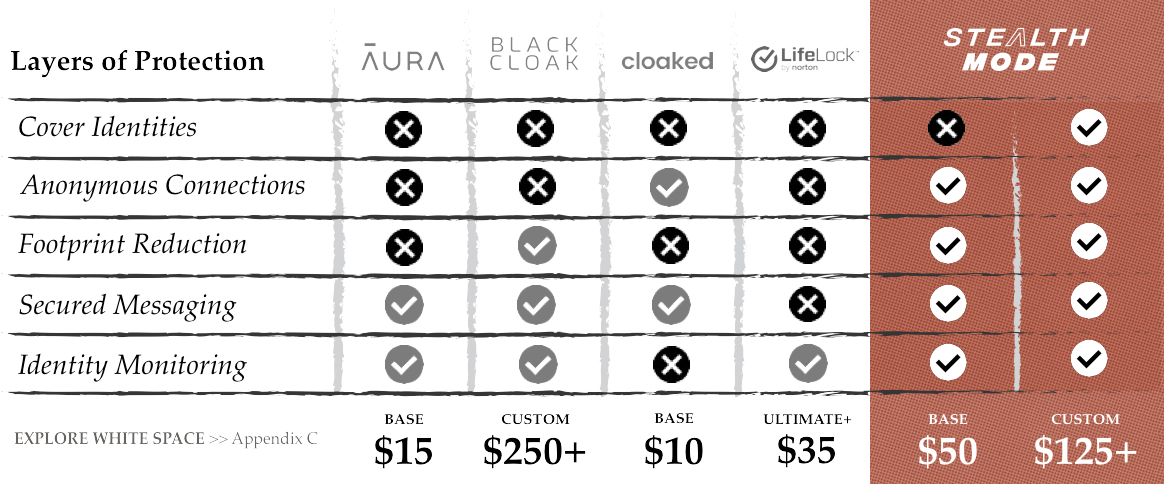
OUR SOLUTION

We’re building the only fully-integrated, 5-layer privacy crime protection in the marketplace. For more than a century, intelligence services successfully shielded people from harm by cloaking identities in anonymity. With StealthMode, you’ can enjoy the same type of proactive strategies that prevent losses before they occur.

Cloak Harbor will calculate a StealthScore to
track progress and inspire vigilance. We believe habits will form
faster with a fun, educational, and rewarding system. We’ll also issue a
tradecraft manual with detailed instructions on achieving near
invisibilty. At our custom level of service, members will leave
the grid thanks to an intelligence-grade cover identity and an
affordable secure phone.
OUR MEMBERS AHEAD
We’ll protect vulnerable and elevated-risk citizens alike.

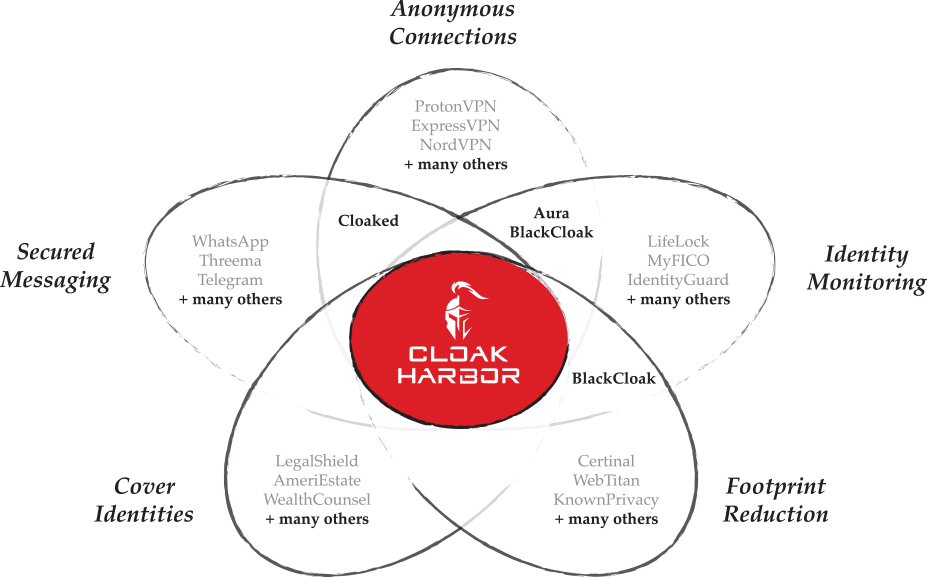
OUR TRADECRAFT
-
Cloak Harbor’s StealthMode is achieved in collaboration with our experienced and reputable partners.